What is LoRaWAN?
LoRaWAN® is a revolutionary Low Power Wide Area Networking (LPWAN) communication protocol that enables seamless wireless connectivity between physical objects and the internet.

Short for
Long Range Low Power Wide Area Network
It is designed specifically for IoT. It enables long-range communication between devices and a central server while consuming minimal power.
Your smart devices can seamlessly communicate regardless of location
How LoRaWAN works?
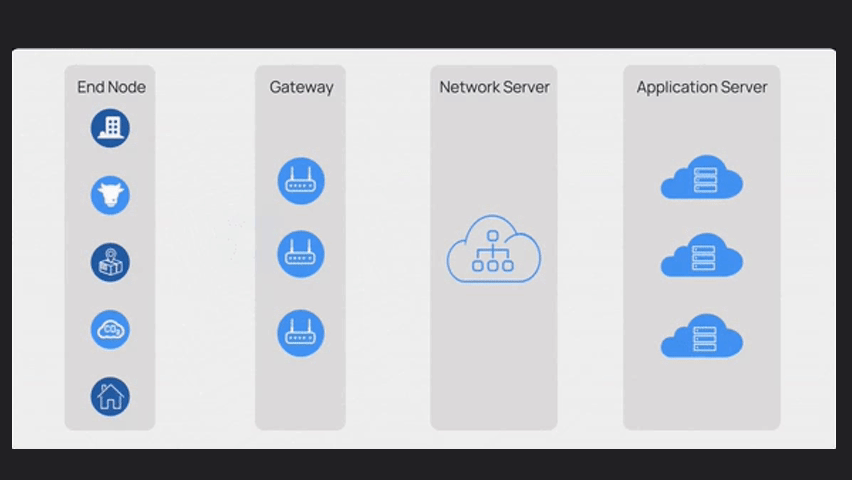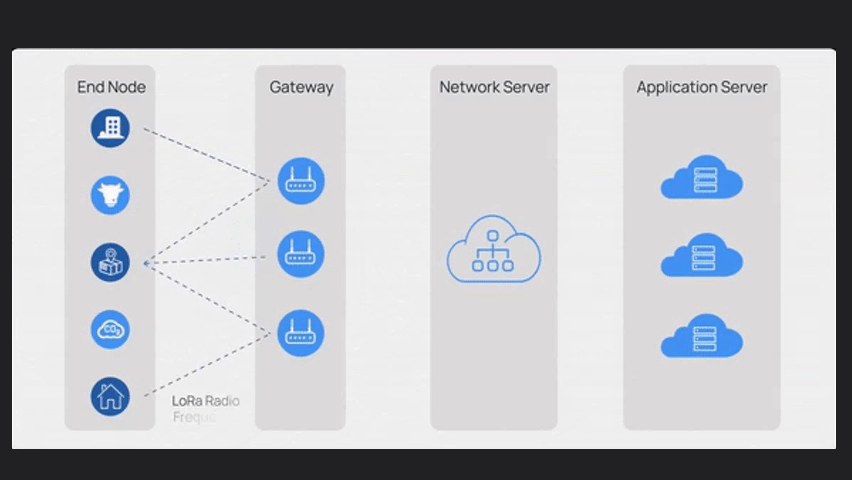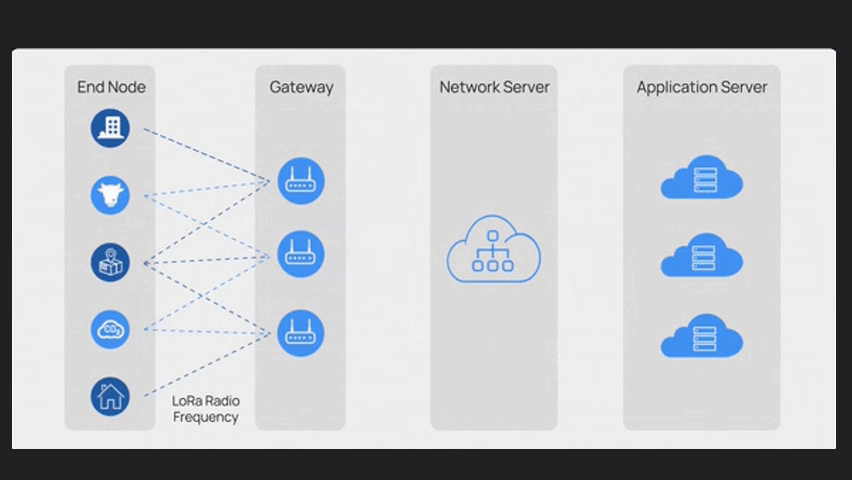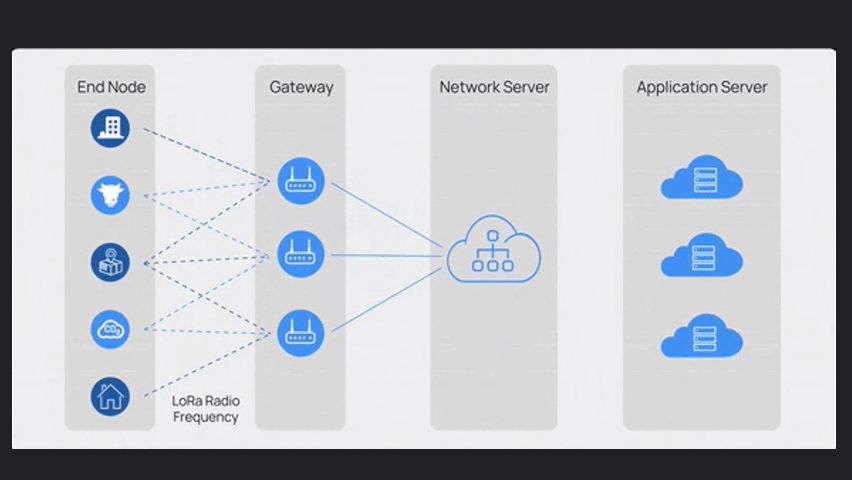
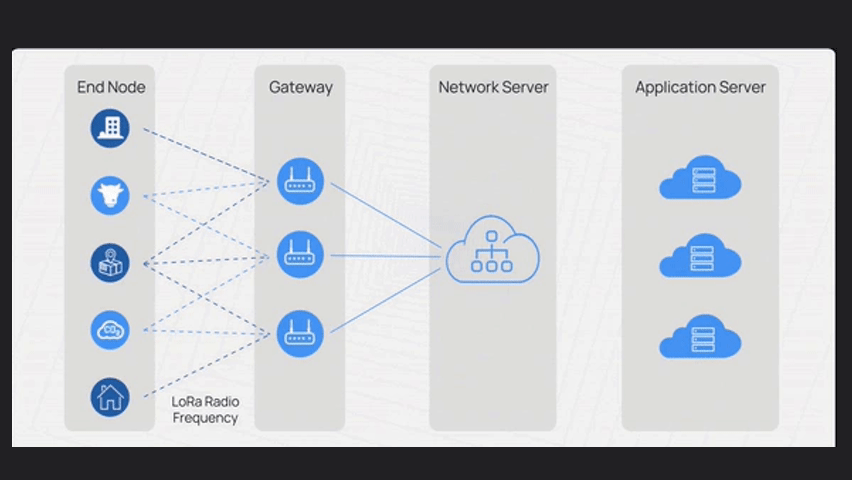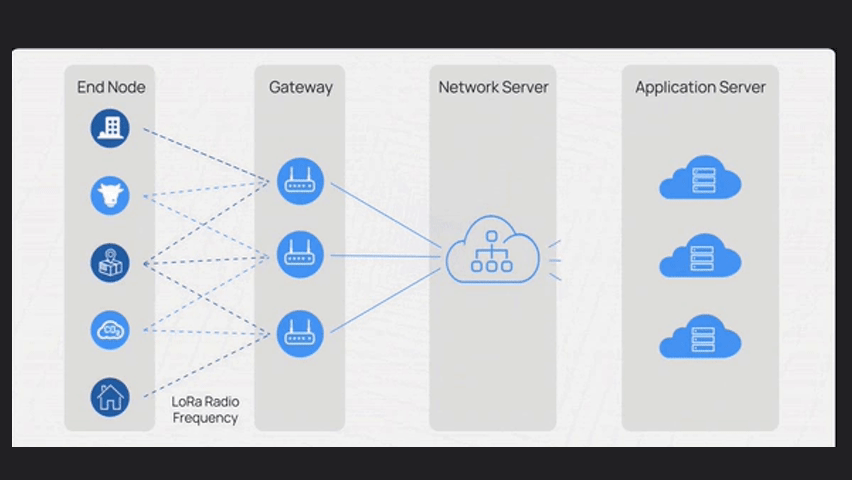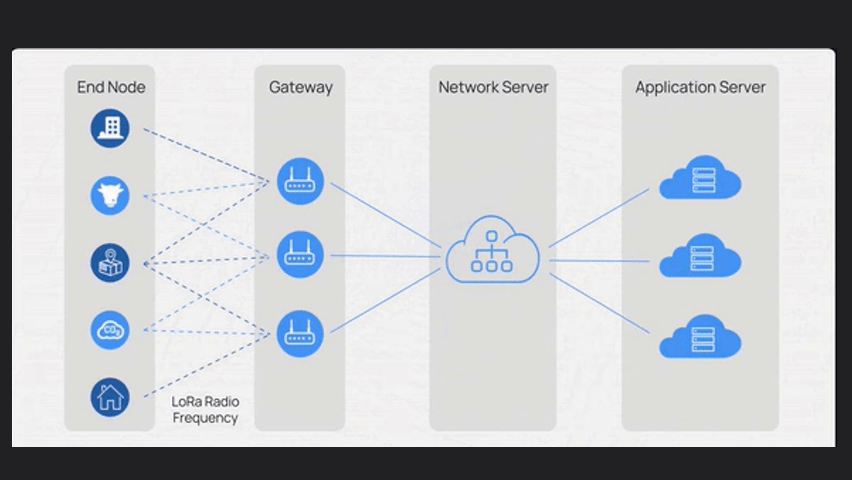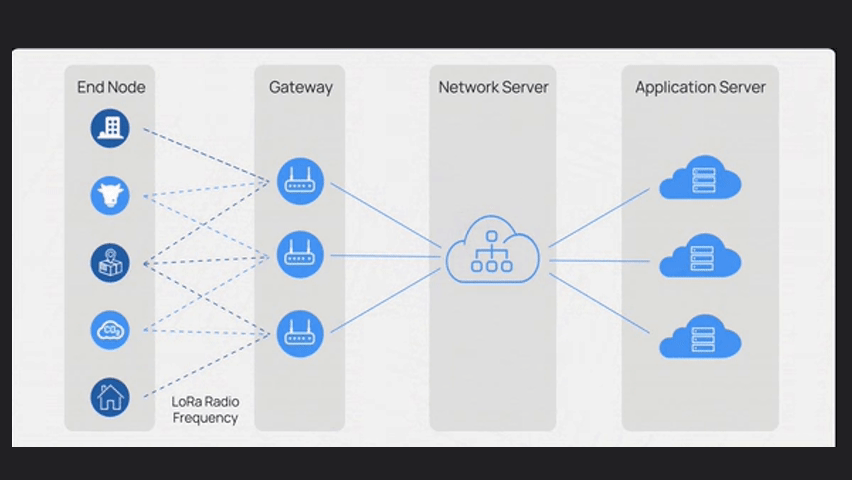
LoRaWAN has four main components:
End nodes, Gateway, Network Server and Application Server
The Network Server, manages communication, authentication, security and data routing.
It receives data from gateways and fowards it to application servers based on predefined rules
Application servers process data, enabling integration, analysis, visualization and interfaces with other systems.
They extract meaningful insights from device data.
Why choose LoRaWAN and its advantages?
One of the key advantages is its exceptional long-range capabilities. The specific distance between the LoRaWAN nodes and the gateway can vary based on factors like the environment, interference end etc, but it can cover vast distances, reaching several kilometers ranging up to 2 km in urban areas and 15 km in rural areas.
This makes it ideal for cost-effective IoT solutions on a large scale.
Another remarkable features of it is its low power consumption.
IoT devices operating on LoRaWAN can run on small batteries for years, reducing the need for frequent maintenance.
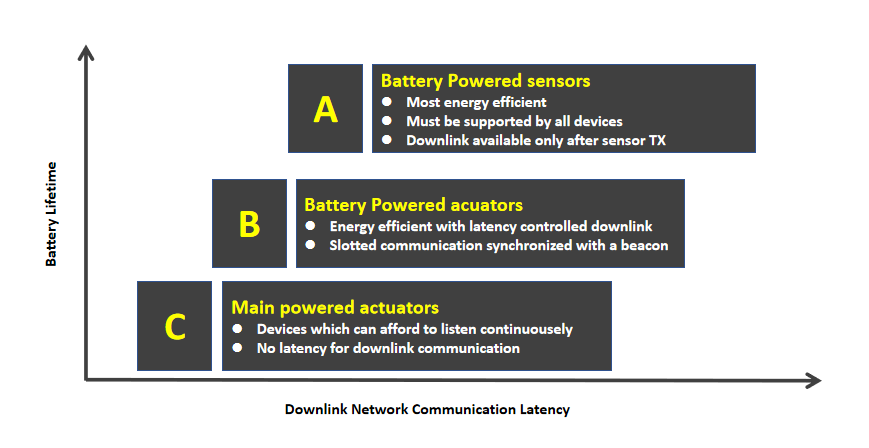
LoRaWAN networks are highly scalable allowing the connection of up to 2000 nodes from a single gateway, handling thousands of devices for future growth and expansion.

Additionally, LoRaWAN ensures secure data transmission through AES-128 encryption, unique keys, authentication, message integrity checks, a secure joining process and regular key updates.
These measures guarantee the confidentiality, integrity and authenticity of data.
Real world applications of LoRaWAN?
LoRaWAN has practical uses in smart building and offices such as IAQ monitoring for improving residents living environments, people counting and occupancy management for optimizing space utilization and smart restroom management for enhacing user experience. Additionally LoRaWAN facilitates power consumption management, boosting energy efficiency.

In agriculture, LoRaWAN allows remote monitoring of soil conditions and irrigation optimization for better crop yields, and promotes sustainable and efficient agriculture.
LoRaWAN is a game-changer in IoT connectivity. Its long-range capabilities, low power consumption, high scalability and security make it a powerful technology for various applications.
From smart cities to agriculture and beyond, LoRaWAN paves the way for a connected future.
FAQs:
LoRaWAN® is a Low Power, Wide Area Network (LPWA) specification designed to wirelessly connect battery-operated devices to the internet. It supports bidirectional communication, end-to-end security, mobility, and localization services. Operating in unlicensed radio frequency bands, LoRaWAN is known for its long-range capabilities (up to 15 km in rural areas), low power consumption, and the ability to connect many devices to a single network. Its architecture includes end devices, gateways, network servers, and application servers, providing a scalable and flexible solution for various IoT applications.
Unlike wired networks, where communication is contained within a cable or fiber, the fundamental challenge of wireless networks is the lack of a physical perimeter around communicating devices. To eavesdrop, capture and replay traffic, modify network traffic, spoof identities, and gain unauthorized access, an attacker only needs to be near the wireless network. Using cryptography, LoRaWAN provides a robust security foundation to thwart these attacks. This security foundation protects network traffic and uses secure device credentials to ensure the confidentiality, integrity, and authenticity of network traffic between LoRaWAN terminals and other network elements.
- Encryption and Integrity Protection: Encryption prevents eavesdropping, while integrity protection prevents capture, replay, and modification of network traffic.
- Secure Device Credentials: Unique device identifiers and secret keys allow device authentication and authorization, preventing identity spoofing and unauthorized network access.
- Advanced Encryption Standard (AES): LoRaWAN security relies on AES, as specified in the NIST FIPS 197 standard.
Annex I of the EU Cyber Resilience Act specifies "security requirements regarding the characteristics of products with digital elements." Since LoRaWAN can be considered a "digital element," this general declaration includes LoRaWAN products. The LoRaWAN security foundation allows for developing a product that meets Appendix I.1.3 requirements. Using OTA firmware updates allows for developing a product that meets Appendix I.1.5. The remaining annex requirements relate to the overall product security and customer engagement programs established by the manufacturer, such as a method for customers to report vulnerabilities.
The best practice to ensure that all LoRaWAN end nodes within a system are unique is to use secure device credentials consisting of properly assigned EUIs and unique root keys. The root key should not be obtainable from the end device itself and should not be printed on the end device or its accompanying documentation. These measures prevent cloning or spoofing of a LoRaWAN terminal within a LoRaWAN system.
A LoRaWAN end device has a secure device credential that includes a 128-bit AES AppKey and an EUI (Extended Unique Identifier) based on an OUI (Organizationally Unique Identifier) assigned by the IEEE Registration Authority. From these, two unique 128-bit AES keys, the Network Session Key (NwkSKey) and the Application Session Key (AppSKey), are derived when the end device joins the LoRaWAN network and interacts with the Join Server. The NwkSKey is shared with the network server, and the AppSKey is shared with the application server used by the LoRaWAN end device.
The authenticity of the sender is verified by the receiver by checking the MIC (Message Integrity Code). This process is known as data origin authentication.
The MIC calculation includes a counter in both the message payload and additional data, whose value can only increase. Therefore, the proof that a message has not been replayed is provided by the receiver verifying the MIC and ensuring the message counter increases message by message.
LoRaWAN networks typically operate in unlicensed Industrial, Scientific, and Medical (ISM) bands. Although licensed-spectrum system providers often imply that ISM bands are unregulated and noisy, these bands are heavily regulated in their respective jurisdictions to ensure fair coexistence of devices using them. The resilient LoRa Spread Spectrum modulation scheme can demodulate a signal down to 17 dB below the noise floor, ensuring optimal performance in the presence of interference, which can occur in any band, licensed or unlicensed.